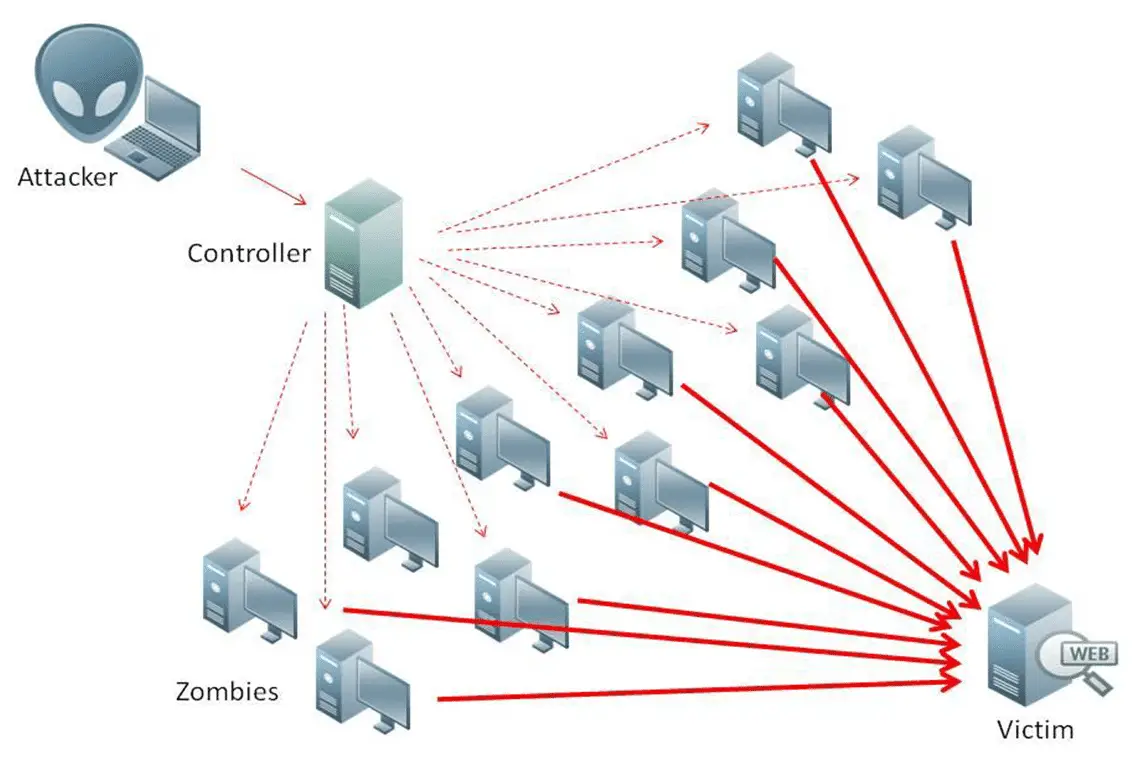
Multiple types of attacks
With the PING command can be executed on the operation of ICMP request, this request is very easy to cause network congestion. DDoS attacks can be done in a variety of ways, ICMP is only one of them.
In addition, there is a Syn attack, launched this attack, in fact, just open a TCP link, then usually connected to a website, but the key is that this operation did not complete the initial handshake, left the server The
Another clever way is to use DNS. There are many network providers have their own DNS server, and allow anyone to query, and even some people are not their customers. And the general DNS is the use of UDP, UDP is a connectionless transport layer protocol. With the above two conditions as a basis, those attackers are very easy to launch a denial of service attacks. All the attackers have to do is find an open DNS resolver, making a virtual UDP packet and forging an address, facing the target site to send it to the DNS server. When the server receives a request from an attacker, it will be true and send a request response to the forged address. In fact, the target site received a group of open DNS resolver on the Internet request and reply, which instead of the botnet attacks. In addition, such attacks have a very large scalability, because the DNS server can send a UDP packet, request a side of the dump, resulting in a large flow of response.
DDoS attacks in a variety of ways
Denial of service was a very simple way of attack. Some people start running on their computer PING command, lock the target address, let it run at high speed, trying to send flooded ICMP request command or packet to the other end. Of course, because of this side of the sending speed changes, the attacker needs a greater bandwidth than the other site. First of all, they will move to a large host of the place, similar to a university server or teaching and research as a large area of bandwidth, and then from here to attack. But the modern botnet in almost any case can be used, relatively speaking, its operation is more simple so that the attack is completely distributed, it is more subtle.
In fact, because of the maker of malware, botnet operation has become a distinct industry chain. In fact, they have already started to rent those meat machines and are charged on an hourly basis. If someone wants to ruin a website, just give these attackers enough money, and then there will be thousands of zombie computers to attack that site. An infected computer may not be able to ruin a site, but if there are more than 10,000 computers at the same time to send the request, they will unprotect server “stuffed.”
How to protect the network
DDoS attacks are varied, hard to prevent when you want to establish a defense system against DDoS, you need to master the variation of these attacks.
The most stupid defense method is to spend a lot of money to buy more bandwidth. Denial of service is like a game. If you use 10,000 systems to send 1Mbps traffic, it means that you deliver 10Gb of data per second to your server. This will cause congestion. In this case, the same rules apply to normal redundancy. At this point, you need more servers, all over the data center, and better load balancing services. Traffic will be distributed to multiple servers, traffic balance, greater bandwidth to deal with a variety of high traffic problems. But the modern DDoS attacks more and crazier, the need for more and more bandwidth, the financial situation is not allowed to put more money. In addition, the vast majority of the time, the site is not the main target, many administrators have forgotten this point.
The most critical piece of the network is the DNS server. It is absolutely undesirable to put the DNS resolver in an open state, and it should be locked to reduce the risk of some attacks. But after doing so, the server is safe? The answer is of course negative, even if your site, no one can link to your DNS server, help you resolve the domain name, which is also the very bad thing. Most of the registered domain names require two DNS servers, but that is not enough. You want to make sure that your DNS server and your website and other resources are in a load-balanced protection state. You can also use redundant DNS provided by some companies. For example, many people use the content distribution network (distributed state) to send files to customers, this is a very good way to resist DDoS attacks. If you need, there are many companies to provide this enhanced DNS protection measures.
If you manage your own network and data, then you need to focus on protecting your network layer, to carry out a lot of configuration. First of all to ensure that all of your routers are able to shield junk data packets, remove some unused protocols, such as ICMP this. Then set up a firewall. Obviously, your site will never let the random DNS server access, so there is no need to allow UDP 53 port packets through your server. In addition, you can let your suppliers help you make some border network settings, block some useless traffic, and ensure that you can get one of the largest and most unobstructed bandwidths. Many network providers give businesses this service, you can contact their network operations center, so that they help you optimize the flow, to help you monitor whether you have to attack.
Similar to Syn’s attacks, there are many ways to stop, such as by giving TCP backlog, reducing the Syn-Receive timer, or using the Syn cache.
Finally, you have to think about how to intercept them before these attacks arrive at your site. For example, modern sites use a lot of dynamic resources. In the case of attack when the bandwidth is relatively easy to control, but in the end is often lost by the database or you run the script. You can consider using the cache server to provide as much as possible static content, but also quickly with static resources to replace the dynamic resources and to ensure that the detection system to normal operation.
The worst case is that your network or site is completely paralyzed, and you should be ready at the beginning of the attack. Because the attack once started, want to stop DDoS from the source is very difficult. Finally, you should be pondering how to make your infrastructure more reasonable and safe, and to focus on your network settings. These are very important.
The post What is DDos attack? appeared first on Penetration Testing. http://ift.tt/2skHHvy http://ift.tt/2aM8QhC